Guide to Performing an Effective Cybersecurity Risk Assessment
Blockchain and IoT | Multi-Agent Systems | AI vs Automation
In today’s digital age, organizations, whether small or big, face an increasing number of cyber threats. From data breaches to ransomware attacks, the threats are increasing in complexity, number, and scale day by day. In order to protect sensitive information, operations, and infrastructure, a cybersecurity risk assessment must be performed. It helps businesses and organizations identify risks, vulnerabilities, evaluate threats, and formulate strategies in order to reduce and manage risk.
In this article, we’ll explore what a cybersecurity risk assessment is, why it is important, what prerequisites are needed to be fulfilled, and how a cybersecurity assessment is performed. Whether you are a cybersecurity professional, an IT manager, or an entrepreneur, understanding and implementing these steps will help strengthen your defense against cybersecurity threats.
What is a Cybersecurity Risk Assessment?
Did you ever wonder what a cybersecurity risk assessment is? It is a systematic and data-driven process aimed at identifying, quantifying, and evaluating potential vulnerabilities and threats to an organization’s digital framework in order to mitigate risks and strengthen security measures. Ultimately, the objective of cybersecurity risk assessment is to prioritize what digital assets are most at risk, what is the likelihood of a security threat to exploit a vulnerability, and what potential consequences these risks would have.
The results of a cyber risk assessment help organizations and businesses prioritize and evaluate security measures, make informed decisions about allocating resources, and comply with legal requirements such as GDPR, HIPAA, or ISO/IEC 27001.
Improper cybersecurity risk management poses threats to any business operation. With an increasing number of mobile networks and Internet of Things IoT devices, the cyber threat dynamics constantly evolve, and organizations discover new risks daily. After conducting an initial cybersecurity risk assessment, businesses must implement ongoing risk management because both their operations and external cyber threat landscapes constantly evolve.
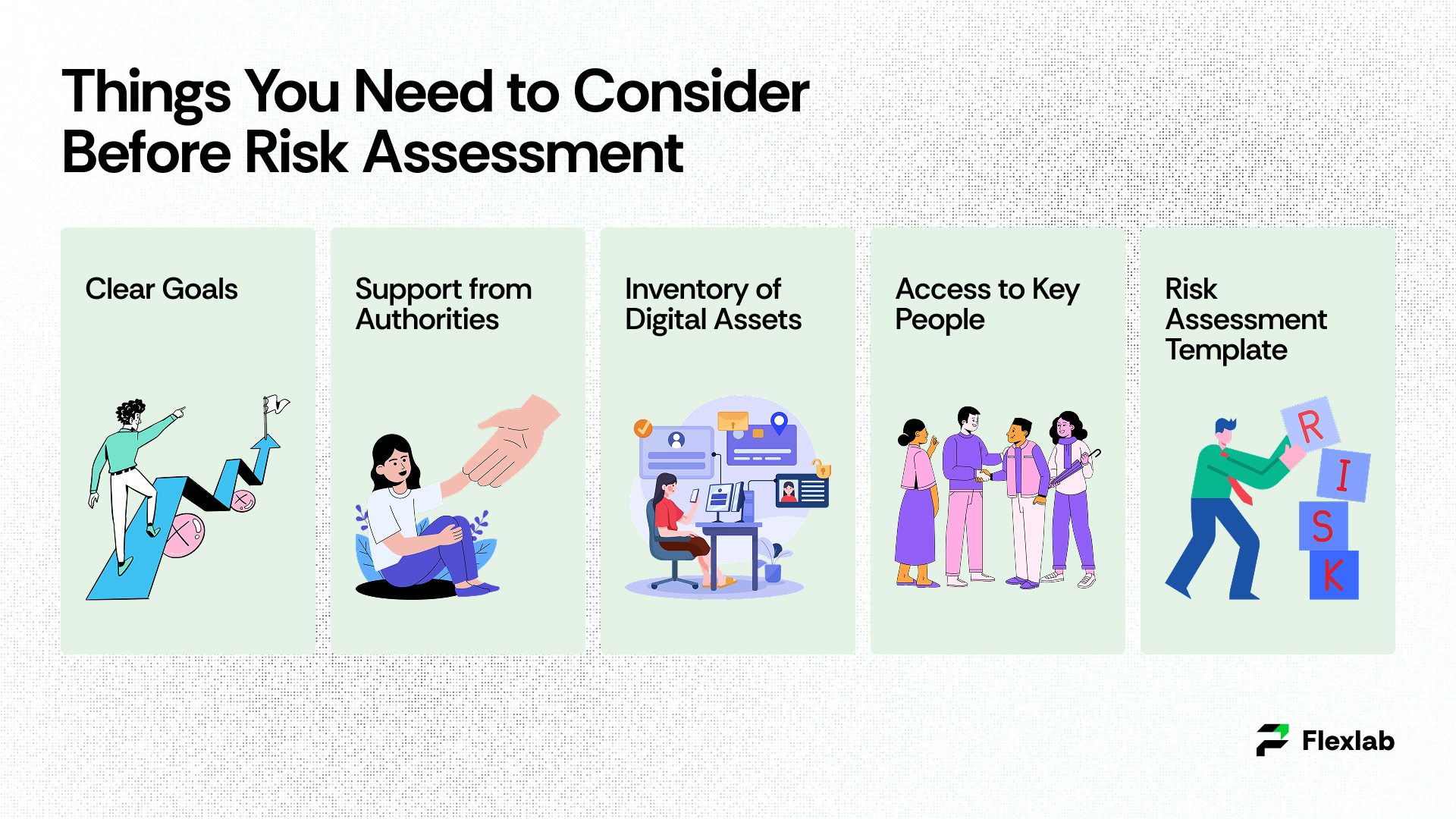
Things to Consider Before Cybersecurity Risk Assessment
Before jumping into the cybersecurity risk assessment, make sure you meet certain prerequisites. Define a clear purpose for conducting this assessment to implement the right security controls. In order to ensure the availability of resources (e.g., time, tools, people, etc), cooperation from top authorities and management is important. Teams must collect a clear and full inventory of the IT environment, including devices, software, databases, and cloud services, before performing the assessment. They must also take inputs from different departments (like finance, IT, HR, etc.) to understand their usage of digital systems and identify where the problem would arise. A simple risk assessment template beforehand can help organize findings. It can be a simple table or spreadsheet with labels.
Step-by-Step Guide to Perform Cybersecurity Risk Assessment
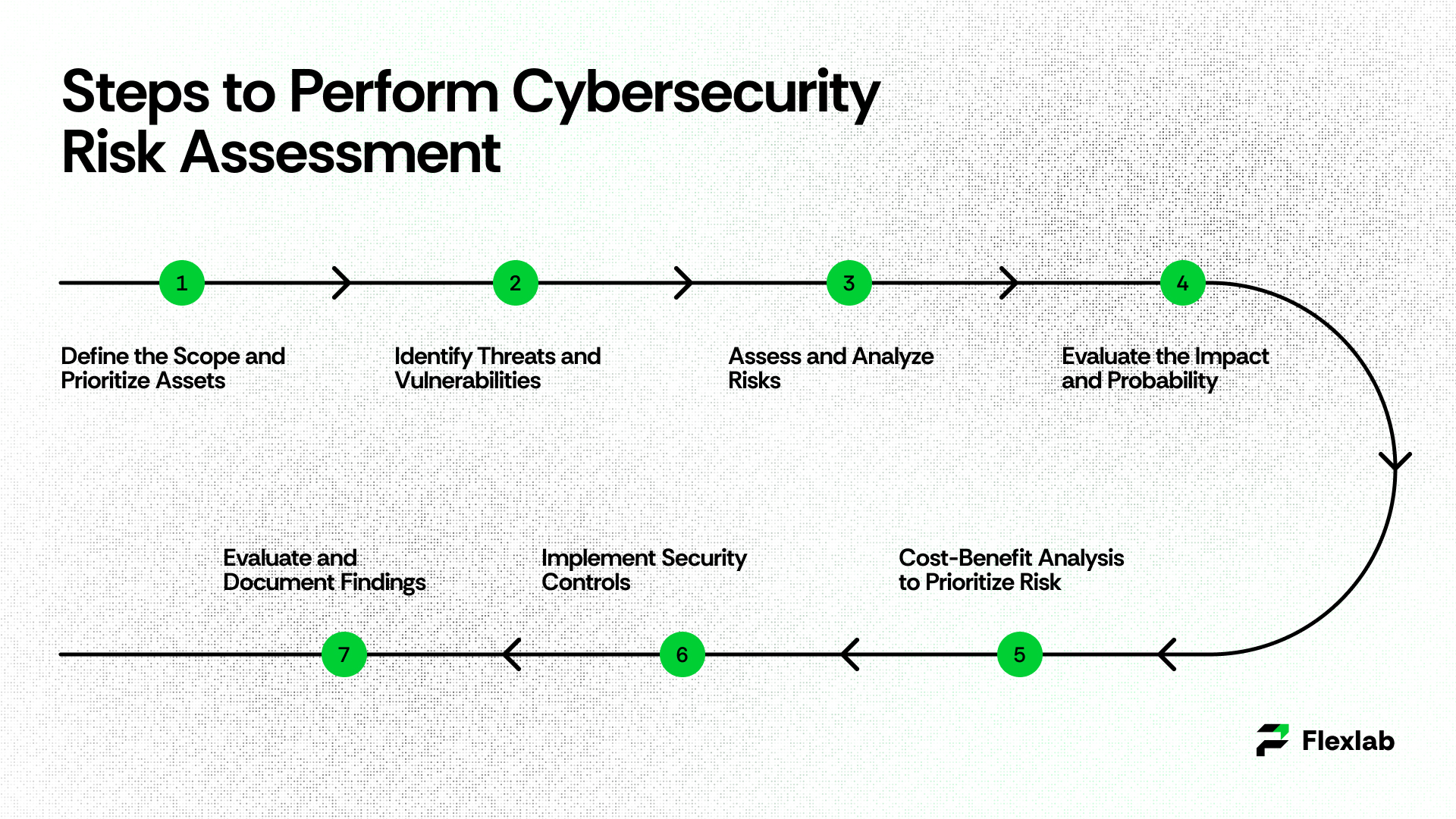
In order to perform an effective cybersecurity risk assessment, security teams need to take into account several structured steps to identify, prioritize, and mitigate risks. The following are the steps;
- Define the Scope and Prioritize Assets
- Identify Threats and Vulnerabilities
- Assess and Analyze Risks
- Evaluate the Impact and Probability of Risks
- Cost-Benefit Analysis to Prioritize Risk
- Implement Security Controls
- Evaluate and Document Findings
1. Define the Scope and Prioritize Assets
Before you dive deep into cyber risk assessment, define the scope of the assets. It can be the whole organization, a single unit, a specific location, or a business operation. In addition to identifying assets, an organization should also evaluate which information or assets are its “crown jewels”. This can be highly confidential client information, or an IP address that is of high value to the organization, an important web application, or an asset. For this specific purpose, the organization needs to make an inventory of all the physical and digital assets that are relevant to the scope as a part of their risk management plan. This might include;
- Hardware framework such as workstations, servers, connected mobile phones, and routers etc.
- Software like operating systems, cloud servers, and applications, etc.
- Data Records like financial records, customer data, and intellectual properties, etc.
- Networks such as users, administrators, third-party vendors, and customers etc.
Once the assets are identified, the next step is to classify the assets depending on the value, sensitivity, and legal standing. Label them as;
- High value assets such as financial records, customer databases, etc.
- Medium value data, such as emails and internal documents, etc.
- Low value information, such as website content
By recognizing the most crucial assets, businesses can now take the next step. Consequently, they can secure these high-value items and prioritize strategies to protect them.
2. Identify Threats and Vulnerabilities
In the second step of cyber risk management, the organization or business identifies all the possible cyber threats and vulnerabilities.
But firstly, the difference between a threat and a vulnerability needs to be clear. A vulnerability represents a weak point within an organization’s IT environment, and a cyber threat can exploit it easily. Some common vulnerabilities include:
- Technical Errors like IT misconfigurations, weak passwords, unpatched applications, etc.
- Human Flaws like improper training, phishing susceptibility, etc.
- Physical Data Security Gaps, like excessive access and administrative rights, unattended devices, unlocked or unprotected server rooms, etc.
Vulnerability scanning or penetration testing can be conducted to scan vulnerabilities that can pose harm to the cybersecurity framework of an organization.
A threat is a tactic or anything that has the potential to exploit a vulnerability to cause harm. Threats can either be internal– coming from an employee or other user or external– coming from a threat actor outside the organization. Here are some common types of cyber attacks:
- Phishing: Social engineering attacks through emails or messages.
- Malware: Viruses, Spyware, Ransomware, or any other attack that leverages the data security systems in a malicious way.
- Distributed Denial of Service Attacks: A DDoS Attack is a threat that tends to interfere with the operation of a network by flooding it with fake internet traffic.
- Insider Threat: Accidental breaches or any threat that originates from within the organization.
- Exploit kits: Any toolkit used to exploit a specific kind of vulnerability in a system.
Frameworks like the MTRE ATT&CK and the National Vulnerability Database (NVD) can be used to identify threats and vulnerabilities to a system.
3. Assess and Analyze Risks
Once the organization identifies its high-priority assets along with specific threats and potential vulnerabilities, it must assess and analyze the corresponding risks based on these two components. While analyzing risks, teams should consider factors like discoverability, reproducibility, and exploitability of vulnerabilities. This step of cybersecurity assessment aims to determine the likelihood and potential impact of a threat in order to analyze and prioritize risks. By effectively assessing this information, the organization can now prioritize risk mitigation strategies.
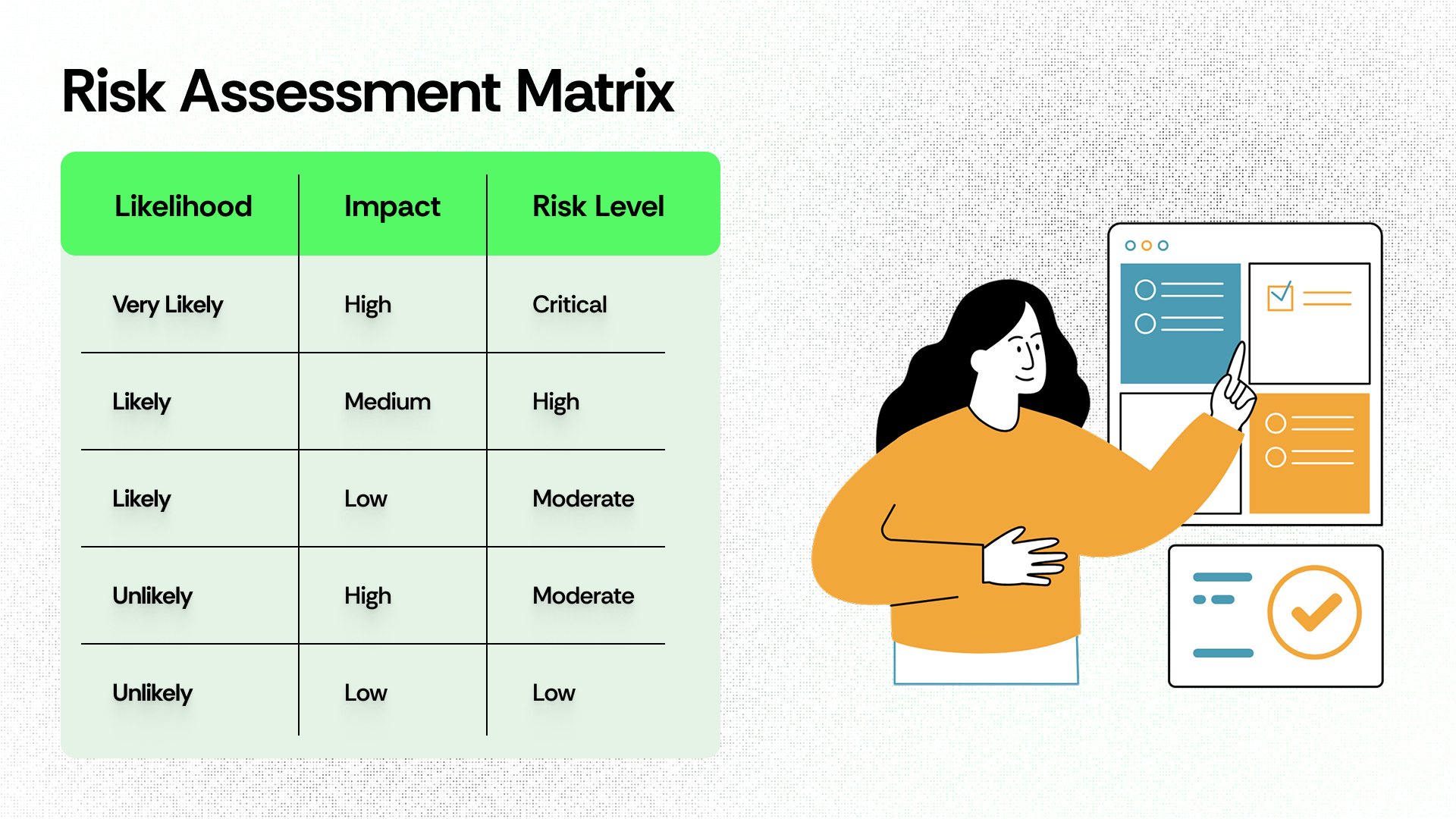
4. Evaluate the Likelihood and Impact of Risks
This step in cybersecurity assessment aims at assessing how likely it is for a threat to exploit a specific vulnerability. The security team can rate it either quantitatively (e.g., rating it from 0 to 10 on a scale) or qualitatively (e.g., labelling it as low, medium, or high). The impact of a threat depends on the loss of integrity, confidentiality, and availability of information. These factors then lead to other outcomes such as financial losses, fines, and legal repercussions from non-compliance. They also lead to reputation damage and operational disruptions.
As a part of this risk management plan, businesses and organizations should therefore design a clear and consistent assessment tool. Moreover, this tool helps them calculate the impact of all vulnerabilities and corresponding threats within their IT environment.
In order to calculate the risk, the risk assessment matrix is used, which works by combining the likelihood and impact of a risk.
5. Cost-Benefit Analysis to Prioritize Risks
In this step, organizations review the vulnerabilities that appeared during the assessment process and prioritize them depending on which vulnerability poses the highest risk to the organization. The highest priority risks should be neutralised first.
Prioritization depends on some specific factors;
- The impact the vulnerability will have on the business if it’s exploited
- Vulnerability score as per the threat intelligence tool
- Ease of exploiting the vulnerability
- The likelihood of the attacker knowing about this vulnerability and of it getting exploited again
In order to prioritize risk, organizations must take into account policies, feasibility, rules and regulations, and their attitude towards risk.
6. Implement Security Controls
Now that the risks are identified and prioritized, organizations develop and implement security controls to mitigate the identified risks. These security controls can be technical, such as firewalls and encryption protocols. Organizations can also implement non-technical security controls, such as organizational policies, employee training, awareness programs, and physical security measures. They must implement preventive and detective security controls by ensuring proper integration and configuration.
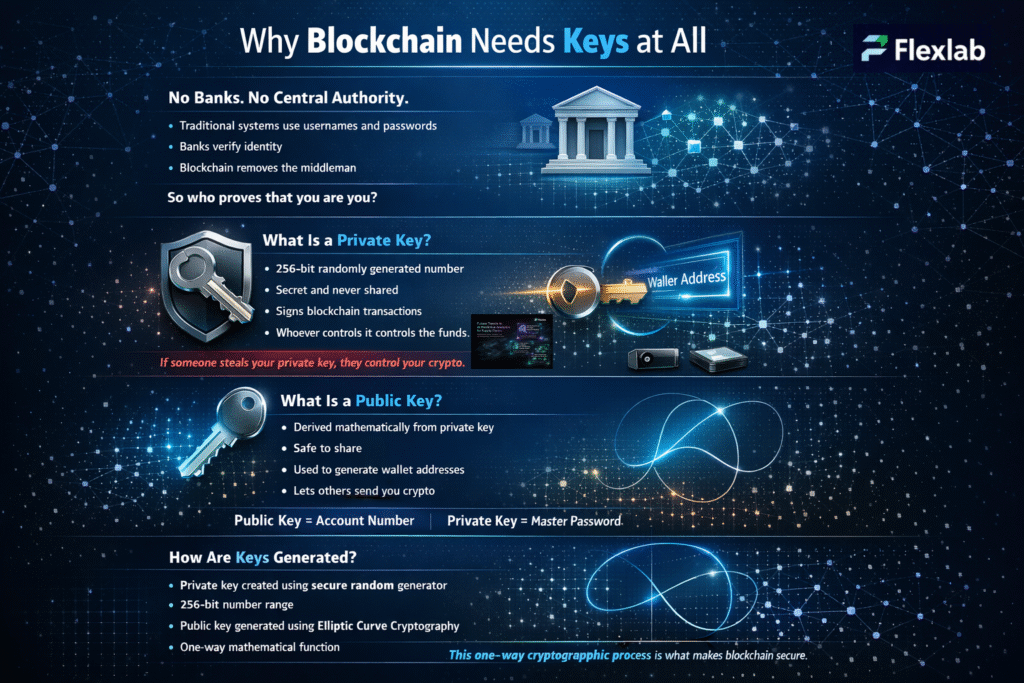
Check out our blog post on Blockchain and IoT: Benefits, Use Cases and Their Challenges to understand data security through blockchain.
7. Evaluate and Document Findings
The final step of cybersecurity risk assessment is to evaluate and document the results. It is where a cyber risk assessment report is created that documents the entire process of assessment, including risk scenarios, results of risk analysis, implemented security controls, and progress status of cyber risk management. This report will serve as a reference for decision-making teams, IT professionals, regulatory bodies, and auditors.
Organizations must understand that cyber risk assessment is an ongoing process that requires regular execution. Moreover, because threat and vulnerability dynamics are evolving day to day, companies should conduct risk assessments frequently. Consequently, this approach not only helps organizations resolve old vulnerabilities but also enables them to detect new ones as they arise.
Why is Conducting Cybersecurity Risk Assessment Important?
With an average cost of USD 4.88 million of data breaches alone in 2024 globally, a cybersecurity risk assessment becomes crucial. Approximately 1 billion emails were exposed to cyber threats in one year, affecting 1 in 5 internet users. The purpose of mentioning these data breach statistics is to highlight the importance of cybersecurity risk assessment for organizations and businesses.
Although organizations and businesses are increasingly relying on artificial intelligence(AI) and business operations, only 24% of gen AI projects are secured. Moreover, in today’s digital world, where cyberattacks are stronger than ever, risk assessment analysis enables businesses to take proactive steps to prevent unauthorized access and avoid the loss of sensitive information.
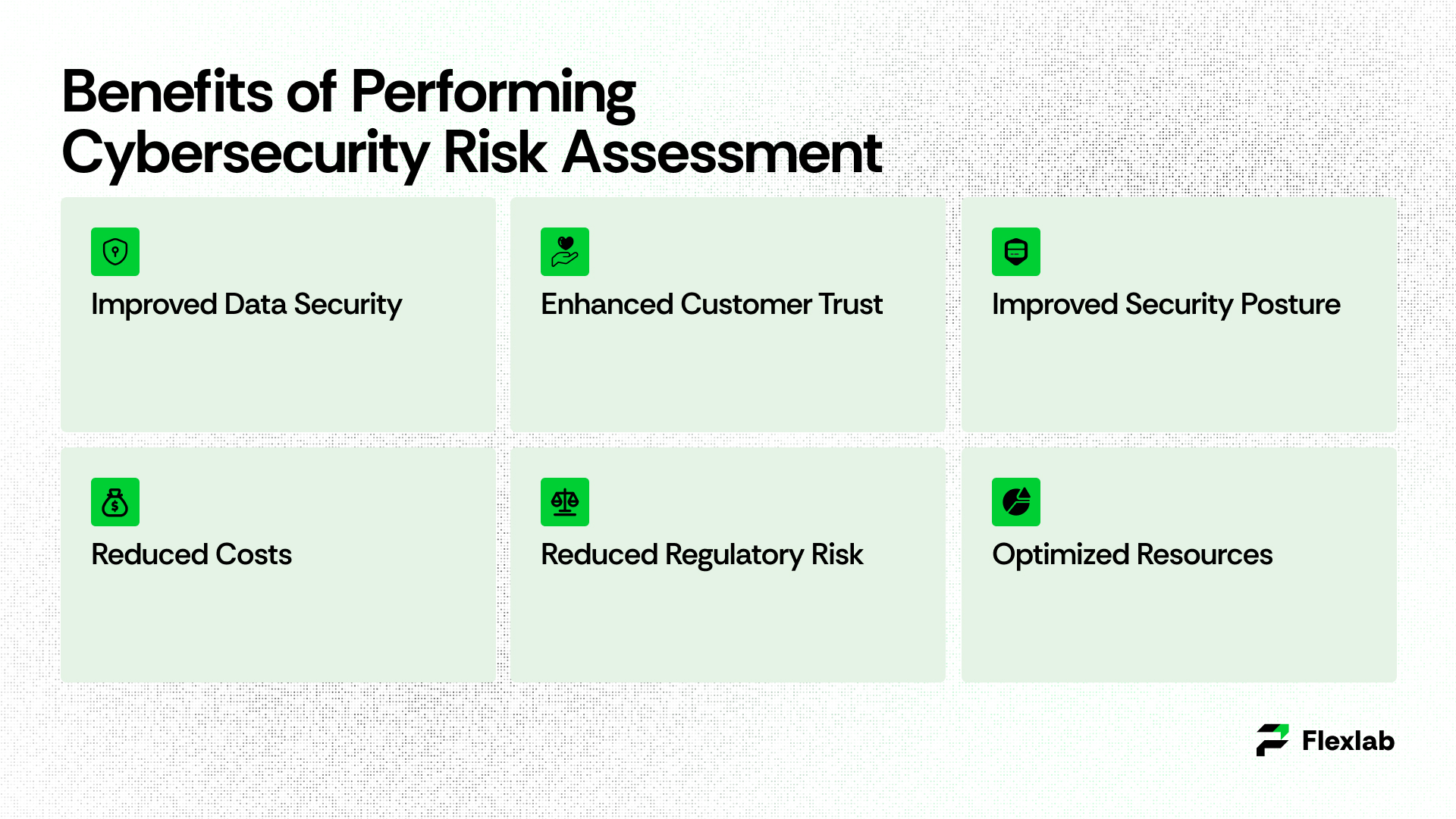
Here are some of the potential benefits that reinforce the importance of conducting a cyber risk assessment;
- Enhanced Customer Trust
- Improved Security Posture
- Reduced costs
- Reduced regulatory risk
- Optimized resources
-
Enhanced Customer Trust
Performing an effective and regular cybersecurity assessment helps build customer trust in the organization. Clients are more likely to do business with companies that are transparent with their digital security and show responsibility in handling sensitive client information.
-
Improved Security Posture
The most apparent benefit of performing a cybersecurity risk assessment is an enhanced security posture of the entire IT environment in an organization. This is achieved by:
- Increased visibility into complete IT assets and applications
- Establishing a complete inventory of user privileges, activity within Active Directory, and identities
- Identification of vulnerabilities across different devices and user identities
- Identification of specific weaknesses that a cybercriminal can exploit.
-
Reduced Costs
Moreover, cyber risk assessments help reduce heavy costs linked with cyberattacks. These costs include system downtime, fines or non-compliance, damage recovery, and loss of reputation among customers.
-
Reduced Regulatory Risk
Therefore, a proper cybersecurity risk assessment helps ensure reduced regulatory risk through reliable compliance with data protection standards and protocols.
-
Optimized Resources
Cybersecurity risk assessment helps identify high-priority activities depending on the likelihood and impact of risks. Moreover, this approach allows for better allocation of limited resources.
Want to Protect Your Digital Space?
When it comes to expert support, Flexlab, a trusted US-based company, provides strategic cybersecurity risk assessment services to organizations, helping them analyze risks, close security gaps, and protect their digital space from continuously evolving threats. With a history of providing effective and reliable results, Flexlab helps corporations reduce costs while strengthening their defense against malicious activities. Flexlab, with their team of experts, will help you get actionable insights within 30 days– or they keep working for you free of cost until they do. Moreover, our experienced cybersecurity specialists work side-by-side with your team to design tailored protection strategies that fit your company’s needs.
Do you want to safeguard your system and data with a detailed cybersecurity risk assessment? Contact us today for a free consultation, review our portfolio, and take the first step towards a safer, more strengthened future for your business.
Want to dive deeper into blockchain app development, AI agents, and multi-agent systems? Have a look at our blog page for detailed insights and expert perspectives.
Ready to Grow Your Business?
📞 Book a FREE Consultation Call: +1 (416) 477-9616
📧 Email us: info@flexlab.io
Concluding Thoughts on Cybersecurity Risk Assessment
In this rapidly evolving digital era, cyber threats are not just for big organizations anymore. Cybercriminals are also targeting even small corporations and businesses like hospitals, schools, and personal websites. An effective cybersecurity risk assessment helps you stay one step ahead of cybercriminals. It does this by prioritizing high-value risks and applying the right security measures to mitigate them.
This doesn’t require technical knowledge or high-end software to get started. It only needs a structured approach, time, team involvement, and commitment to protect your organization’s digital space. If done right, a cybersecurity risk assessment doesn’t just protect your organization’s digital assets. It also makes it smarter and resilient in the face of a constantly evolving digital world.
What are the methods of risk assessment in cybersecurity?
In cybersecurity, risk assessment can be performed in different ways. Qualitative assessment analyzes risks using a simple scale and labels them low, medium, or high. On the other hand, quantitative assessment helps prioritize risks using numbers and cost estimates to calculate impact and likelihood. Some organizations also use a hybrid approach to secure their assets. Finally, organizations perform vulnerability assessments to scan systems and fix security flaws before attackers exploit them.
What is the risk assessment tool for cybersecurity?
A risk assessment tool is a software that helps identify, quantify, and manage potential security risks in an organization's systems. NIST, ISO 27005-based tools and platforms like RiskLens and CSET are some common examples of risk assessment tools for cybersecurity.
What is the Take 5 assessment tool?
The Take 5 risk assessment tool is a quick safety checklist. It is used to identify and minimize risks before starting a task. The process involves 5 simple steps: stop and think, look for hazards, assess the risk, control the risk, and perform the job safely. It is mostly used in construction and industrial work environments. Moreover, this tool is significant for being quick, simple, and easy for anyone to use, even without any special training.






















3 Responses