Hot Wallet vs Cold Wallet: How to Pick the Right One
Public vs Private Blockchain | White Label Crypto Exchange | Web3 Technology
Are you worried about choosing the wrong crypto wallet and unsure whether a hot wallet vs cold wallet is best for keeping your digital assets safe? If you hold any cryptocurrency, you already play a major role in your own security. A crypto wallet is the tool that gives you control by storing the keys that prove you own the blockchain coins.
Most people quickly encounter the choice between hot wallet vs cold wallet, and this distinction shapes everything from convenience to long-term security. For example, hot wallets provide fast access to your funds, DeFi platforms, and NFTs. In contrast, cold wallets keep your keys offline, therefore offering stronger protection.
With millions now using crypto and billions already lost to hacks, therefore, this decision matters more than ever. This guide explains how each wallet works, how keys protect your assets, how to pick the one that fits your habits, and which setup will matter most in 2026.
What Are Crypto Wallets and How Do They Work
A crypto wallet is more than a place to hold digital assets. It is a secure form of digital wallets powered by blockchain technology. It manages public keys and private keys, which act as proof of ownership.
Understanding what are crypto wallets is essential because these tools allow users to send, receive, and control their cryptocurrency without relying on a bank or central authority.
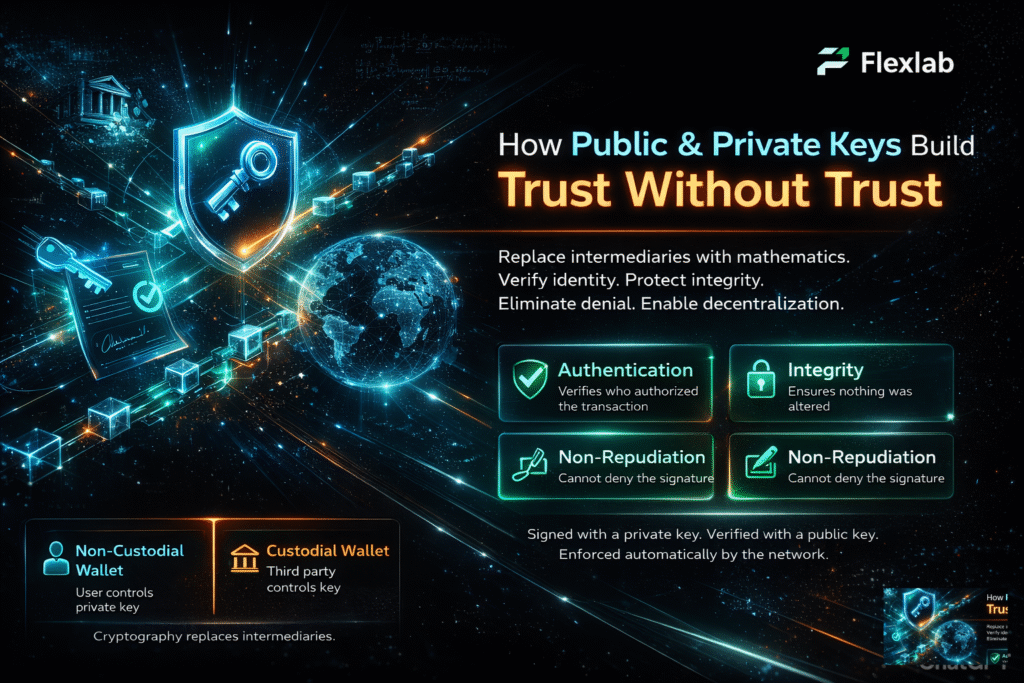
Cryptographic hashes play a crucial role because they create tamper-resistant digital signatures that secure transactions. Consequently, wallets rely on these hashes to validate ownership, ensuring that crypto transactions remain safe and verifiable across global blockchain networks.
-
Public & Private Keys: The Invisible Locks Protecting Your Crypto
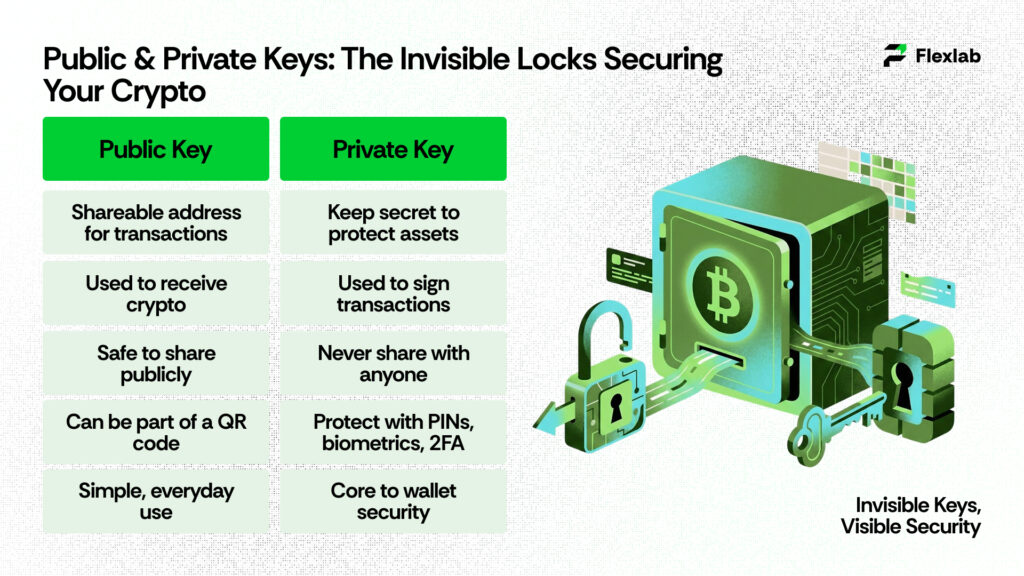
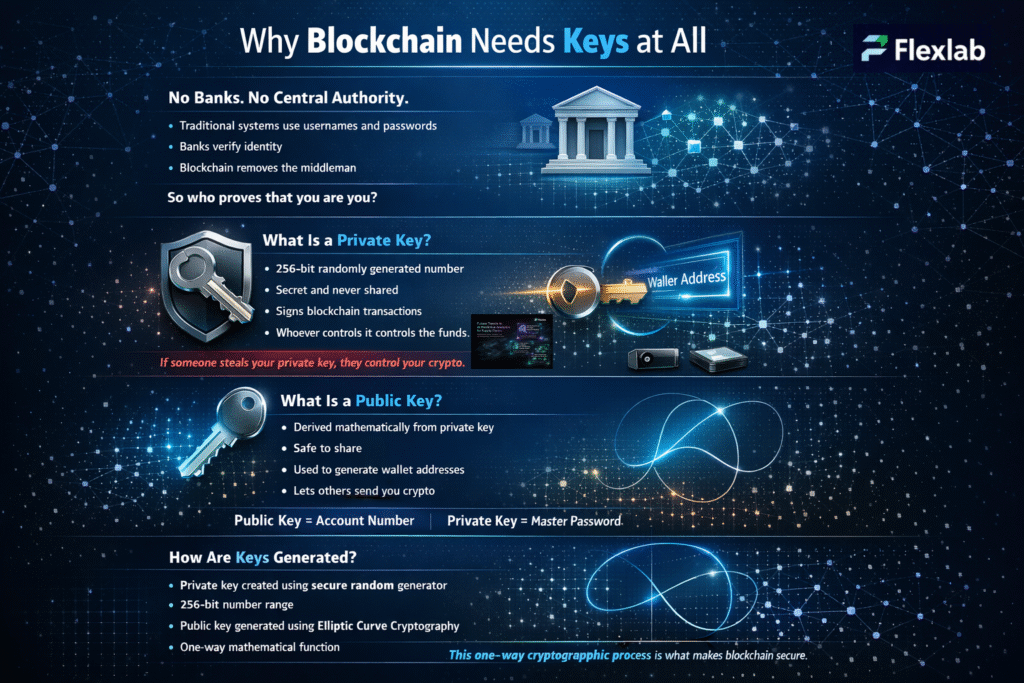
To understand hot and cold wallets, you must first know how public and private keys work. These two elements function as a digital lock-and-key system that keeps crypto secure on the blockchain.
Public Key
A public key is similar to a bank account number. Specifically, it is safe to share, as it is used to receive cryptocurrency and helps generate the wallet address. In other words, it identifies a wallet on the blockchain without exposing any security details.
Private Key
A private key is like a highly sensitive PIN. Therefore, it must never be shared, because it provides complete control over your funds. Additionally, it is used to sign and authorize transactions, and consequently, anyone who gains access to it can move the crypto.
There is no customer support, no fraud reversal, and no undo button if a private key is compromised. As a result, selecting the right wallet becomes a critical security decision. Moreover, since the primary purpose of wallets is to store and protect the private key, they must also enable transactions securely and efficiently.
-
How Wallets Keep Your Crypto Safe Or Put It At Risk
Crypto wallets protect private keys in different ways. Specifically, hot wallets store keys on devices like phones, laptops, or browser extensions. While they provide fast access when online, they are also more exposed to malware, phishing, and other cybersecurity threats.
Cold wallets store keys offline in a hardware device. As a result, they reduce online threats and offer stronger protection for long-term storage. Although they require extra steps to use, they still provide greater security. Therefore, understanding this balance between convenience and safety is essential for safeguarding crypto assets.
-
Types of Crypto Wallets
Crypto wallets come in two main types, each storing and protecting keys differently:
- Hot Wallets: Online and connected to the internet. Often available as mobile apps or browser extensions.
- Cold Wallets: Offline, usually hardware devices. Offer stronger protection for long-term storage.
Both types interact with the blockchain technology network, yet they differ in terms of security and convenience. Therefore, the key question for any crypto user is simple: Which wallet is best for keeping crypto safe—hot wallet vs cold wallet?
What Are Hot Wallets and How They Fit into Daily Crypto Life
Hot wallets are decentralized applications connected to the internet. They are ideal for users who require quick access to funds or frequently interact with NFT marketplaces, decentralized finance (DeFi), or web3 platforms.
Think of a hot wallet like the wallet you carry every day, ready whenever it’s needed.
How Hot Wallets Work
Hot wallets store private keys in software on a browser, desktop, or mobile device. Being online lets users send, receive, and manage crypto instantly.
When a transaction is made:
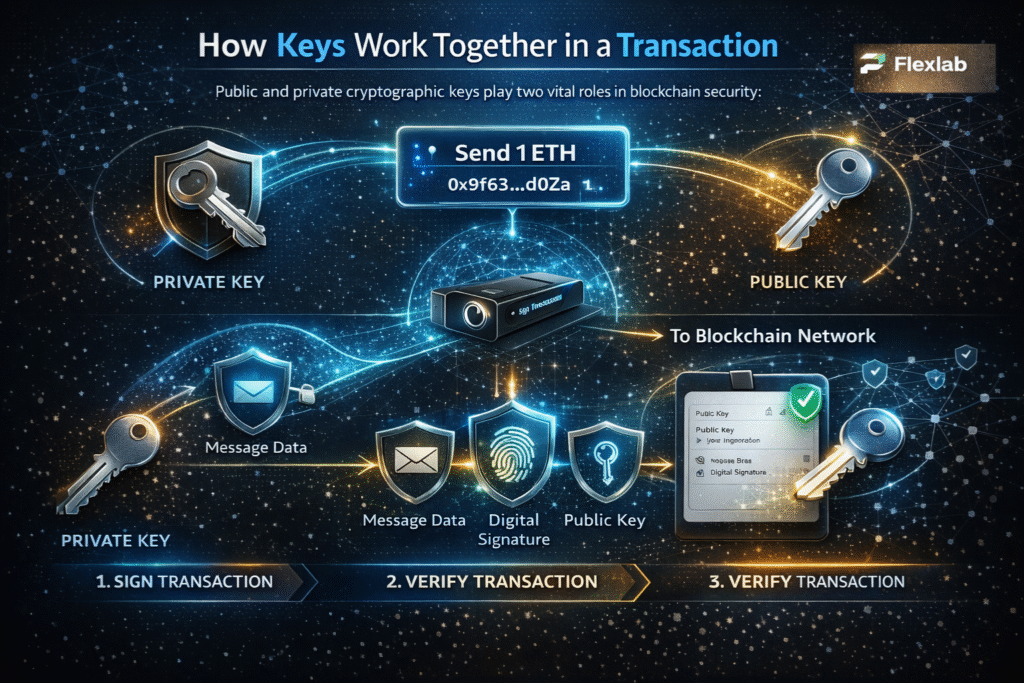
- The private key signs the transaction, proving ownership.
- The wallet broadcasts it to the blockchain network.
- Blockchain nodes verify it using cryptographic rules.
- Once approved, the transaction is added to the blockchain.
Therefore, this online connectivity makes hot wallets extremely convenient. They enable quick token swaps, staking, NFT trading, and seamless interaction with Web3 platforms, all without requiring device switching or waiting for manual approvals.
Types of Hot Wallets
Hot wallets come in different forms, each offering varying levels of convenience and security.
1. Mobile Wallets
Apps like MetaMask Mobile or Trust Wallet run on smartphones. They provide quick access to crypto, staking, DeFi apps, and NFT marketplaces on the go. They are user-friendly but depend on the security of the mobile device.
2. Desktop Wallets
Software such as Electrum or Exodus runs on computers. Desktop wallets offer advanced features, including portfolio tracking and exchange integration. Their security relies on the computer’s protections.
3. Web/Browser Wallets
Browser extensions, such as MetaMask, or exchange-based web wallets, connect directly to decentralized applications and blockchain services. While they are convenient, they are also more exposed to phishing and browser attacks.
Top Benefits of Hot Wallets
Hot wallets are built for convenience and fast crypto management, making them ideal for everyday users. Key advantages include:
- Instant Access to Funds: Send, receive, or swap crypto immediately, perfect for traders and active users.
- Beginner-Friendly Setup: Easy to install and simple to use, making them great for newcomers.
- Seamless DeFi & NFT Integration: Connect quickly to staking platforms, DEXs, token swaps, and NFT marketplaces.
- Low or Zero Cost: Most hot wallets are free, making them ideal for managing small to medium-sized crypto amounts.
- Highly Portable: Mobile wallets like MetaMask and Trust Wallet allow management anywhere, at home, or on the go.
- Supports Multi-Token Portfolios: Store and manage coins and tokens from multiple blockchains in one place.
Major Risks of Hot Wallets
Hot wallets offer convenience, but they carry significant security risks:
- Hacking Vulnerability: Private keys on internet-connected devices can be targeted by hackers.
- Dependence on Device Security: Malware, viruses, or lost/stolen devices can compromise crypto.
- Exchange-Related Risks: Exchange-based wallets face risks such as platform hacks, withdrawal freezes, or insolvency.
- Phishing & Social Engineering: Scammers use fake sites, wallet pop-ups, and emails to steal seed phrases or login details.
Essential Security Tips for Protection
Enhance crypto safety with these tools:
- Identity Protection PINs can add a personal layer of security to prevent unauthorized access.
- Two-Factor Authentication (2FA) strengthens login security with an extra verification step.
- Multi-Party Computation (MPC) Wallets distribute key control across multiple parties for sensitive transactions.
However, these measures don’t eliminate all risks, but they significantly reduce exposure to common attacks.
Cold Wallets: Offline Security for Long-Term Storage
Cold wallets store private keys offline, providing maximum safety. Transactions can even use quick response code signing to simplify offline operations.
How Cold Wallets Work
A cold wallet stores private keys within a physical device, such as a USB-style hardware wallet. When a transaction is made, it is first prepared on a computer or phone, and then signed offline by the cold wallet. Importantly, the private keys never leave the device. Finally, once signed, the transaction is broadcast to the blockchain.
Types of Cold Wallets
Cold wallets come in several forms, each offering strong offline protection:
1. Hardware Wallets
Devices like Ledger Nano X or Trezor store private keys offline. Transactions are signed on the device, so keys never touch the internet. They are highly secure, portable, and considered the gold standard for serious investors.
2. Paper Wallets
A physical printout of public and private keys can serve as a secure option. Although it is immune to online threats, it is still vulnerable to loss, theft, or damage. Therefore, it is best used as a backup or secondary storage method.
3. Air-Gapped Devices
Offline computers or USB devices are used solely to sign transactions without requiring an internet connection. Extremely secure but requires technical knowledge.
Top Benefits of Cold Wallets
- Cold wallets keep private keys offline, offering the highest level of protection. They are ideal for long-term investors and high-value portfolios.
- Maximum Offline Security: Keys never touch the internet, protecting against hacking, malware, spyware, and phishing.
- Perfect for Long-Term Storage: Safely hold crypto for months or years without online risk.
- Full Self-Custody: Maintain complete control, no exchanges, third-party risks, or centralized dependence.
- Multi-Signature & MPC Security: Advanced wallets allow multiple devices or parties to approve transactions for extra security.
- Peace of Mind: Offline keys provide serious investors with confidence that their assets are safe.
Main Risks of Cold Wallets
Meanwhile, cold wallets are highly secure, but they have limitations that affect convenience, usability, and cost:
- Higher Upfront Cost: Hardware wallets require an initial investment, unlike free hot wallets, which may not suit casual users.
- Less Convenient for Daily Transactions: Transactions require connecting the device, confirming actions, and following multiple steps. Quick swaps or routine transfers are slower.
- Physical Damage or Loss: Cold wallets can be damaged by fire, water, impact, or misplacement. Moreover, losing the device without a properly stored seed phrase means that your funds become permanently inaccessible.
- Technical Setup Required: New users may struggle with seed phrases, wallet restoration, passphrases, and security steps. Mistakes during setup can result in loss of access.
Highly Recommended Security Tips
To strengthen protection, cold wallet users should employ multiple layers of cybersecurity when managing long-term assets. Protect a cold wallet with these steps:
- Secure Backup: Store seed phrases in a fireproof safe or use distributed storage.
- Enable Passphrase Protection: Adds an extra layer of security to the wallet.
- Use Hot Wallets for Daily Use: Keep long-term assets offline and small amounts in a hot wallet for everyday use.
This approach combines convenience with maximum security.
Hot Wallet vs Cold Wallet: The Ultimate 2026 Comparison
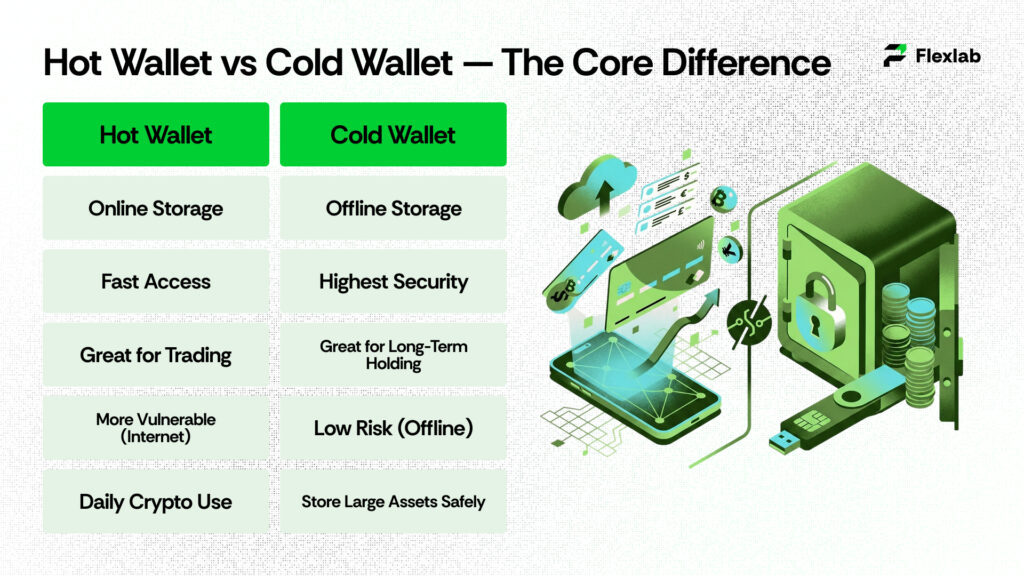
The differences between a cold wallet vs hot wallet become clearer when you compare their security, convenience, and use cases. All wallets are not the same. Hot wallets prioritize speed and convenience, perfect for daily transactions and active trading. Cold wallets focus on security, keeping assets offline for long-term protection. Understanding their strengths and trade-offs helps protect investments while staying flexible in a fast-moving crypto market.
| Feature | Hot Wallet | Cold Wallet |
| Connectivity | Online | Offline |
| Security Level | Moderate; vulnerable to cybersecurity threats | Very high; immune to online hacking |
| Accessibility | Instant access; ideal for trading and daily use | Slower access; best for long-term storage |
| Best For | Frequent transactions, DeFi, NFT marketplaces | Large holdings, long-term investors, cold storage cryptocurrency |
| Cost | Usually free or minimal fees | Paid hardware wallets; paper wallets are free but less convenient |
| Private Key Storage | Stored online; risks if device/exchange compromised | Stored offline; keys never touch the internet |
| Integration | Works seamlessly with dApps, exchanges, and DeFi platforms | Can integrate via QR code or wallet connect, but less convenient |
| Recovery & Backup | Easy; depends on app/exchange backup | Requires careful storage of seed phrases or backup devices |
| Risk Level | High for large amounts | Very low for long-term security |
| Recommended Use | Day-to-day trading and interactions | Long-term holding, cold wallet storage, and maximum security |
A simple rule to remember is that if you engage in frequent trading or NFT/DeFi interactions, a hot wallet is more suitable. In contrast, larger, long-term holdings should use a cold wallet for maximum security and peace of mind.
Choosing the Right Wallet Strategy for 2026
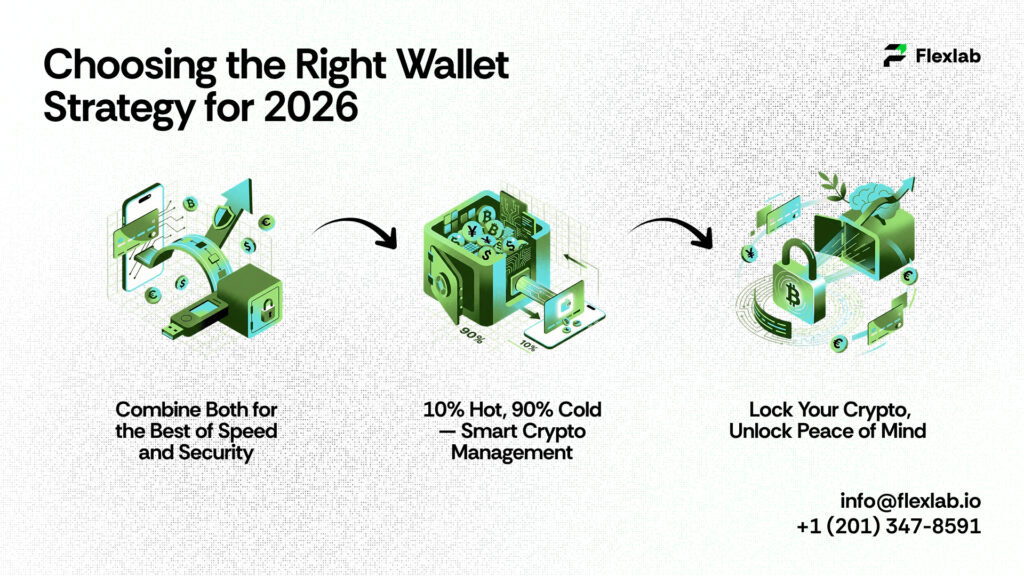
Selecting the right wallet is about more than convenience or security; in fact, it also depends on your habits, as well as your risk tolerance and overall crypto goals. Many users adopt a hybrid approach, combining a hot wallet vs cold wallet for the best of both worlds.
-
Hot Wallet for Everyday Transactions
A hot wallet acts like your digital pocket money, always online for instant access. Use it for:
- Daily trading or small crypto spending
- Participating in NFT drops or marketplaces
- Quick interaction with DeFi protocols
- Managing multiple types of tokens without offline devices
For added security, hot wallets are convenient; however, they also expose your keys to cybersecurity risks. Therefore, it is important to enable strong protections, such as PINs and two-factor authentication (2FA).
-
Cold Wallet for Long-Term Savings
A cold wallet works like a digital safe. It keeps keys offline, protecting assets from hackers and malware. Use it for:
- Large crypto holdings
- Long-term investments
- Protecting assets from online threats
- Advanced security (multi-party computation or passphrases)
Cold wallets may feel slower, but they provide peace of mind. Hardware devices or QR-code signing can simplify offline transactions.
-
The Hybrid Wallet Approach
Combine both strategies:
- Keep a hot wallet for small, daily transactions
- Store most assets in a cold wallet for long-term security
For example, 10% of crypto is in a hot wallet for trading, 90% in cold storage for protection. This approach strikes a balance between speed, convenience, and security.
-
How to Stay Safe with Any Wallet
Your crypto is only as secure as the habits you practice. Follow strong security protocols by protecting private keys and seed phrases, enabling PINs, biometric authentication, and two-factor authentication (2FA). To enhance security, use offline methods for cold wallet transactions, and always double-check URLs when connecting hot wallets to dApps or Web3 platforms. Additionally, keep your devices updated and consider multi-party computation wallets for extra protection. By regularly reviewing your setup and following best practices, you can ensure that your funds remain safe and accessible.
Flexlab Wallet Solutions: Safeguard Your Crypto in 2026

From managing a few tokens to handling millions in crypto, Flexlab provides custom wallet solutions that protect your assets and streamline digital operations. By using advanced security features, such as multi-signature wallets, MPC, cold storage, and biometric authentication, your crypto stays safe. At the same time, it remains ready for DeFi platforms, NFT marketplaces, and multichain ecosystems. Get started with Flexlab today to safeguard your crypto assets and future-proof your investments.
Ready to Grow Your Business?
📞 Book a FREE Consultation Call: +1 (416) 477-9616
📧 Email us: info@flexlab.io
Explore our proven expertise through our portfolio. To inspect real-world projects where we implemented secure crypto solutions, dive deeper into our services. To experience how we custom-build wallets for DeFi platforms, NFT marketplaces, and multichain ecosystems. Check out our blog to gain expert insights and strategies to protect and grow your crypto assets. Connect with us on LinkedIn to stay updated with industry trends, success stories, and professional insights. Elevate your digital strategy. Contact us to explore custom-built solutions designed to scale your business.
Recommended Reads from Flexlab Blog:
- What are NFTs and How Do They Work in Real Life
- Benefits of Using a White Label Crypto Exchange for Startups
- Public vs Private Blockchain: Which is Better for Your Business
Closing Insights: Hot Wallet vs Cold Wallet
Hot wallets provide speed and convenience for daily cryptocurrency activities, such as trading, DeFi, and NFT interactions. On the other hand, cold wallets offer maximum security, making them ideal for long-term storage and high-value holdings. The most effective approach is a hybrid system, utilizing a hot wallet for everyday transactions and a cold wallet to safeguard the majority of your funds. This way, your crypto stays secure, easy to access, and prepared for whatever the future holds in 2026.
FAQs
Q1: How to set up a crypto wallet?
Setting up a crypto wallet is simple and depends on the type you choose. For a hot wallet, you can download an app like MetaMask, Trust Wallet, or Coinbase Wallet, create an account, and make sure you securely save your seed phrase. For a cold wallet, you set up a device like Ledger or Trezor, write down the seed phrase, and store it offline. Then you can safely transfer crypto from exchanges or hot wallets for long-term storage.
Q2: Can I recover crypto if I lose my hardware wallet?
Yes, recovery is possible if you have securely backed up your seed phrase. Hardware wallets such as Ledger or Trezor generate a recovery phrase during setup, which allows you to restore funds on a new device. Never store this phrase online or in cloud storage. Keeping it offline ensures your crypto remains safe even if the device is lost or damaged.
Q3: What is a wallet address?
A wallet address is a unique string of letters and numbers that you use to receive your cryptocurrency. It is generated from your public key and, therefore, is safe to share with others when someone wants to send you crypto. However, your private key must always remain secret, because it gives full access to your funds. Think of it like your bank account number in the blockchain world.





















2 Responses